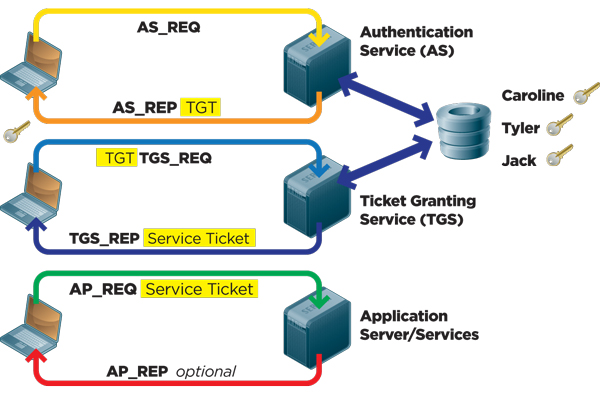
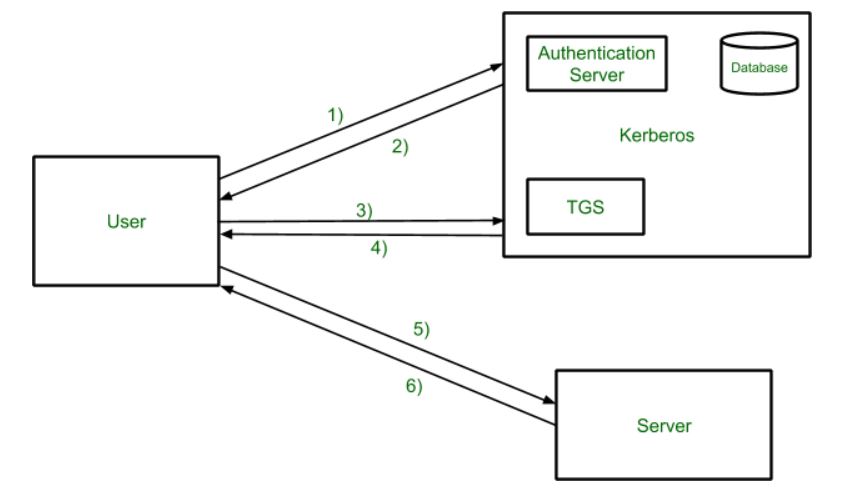
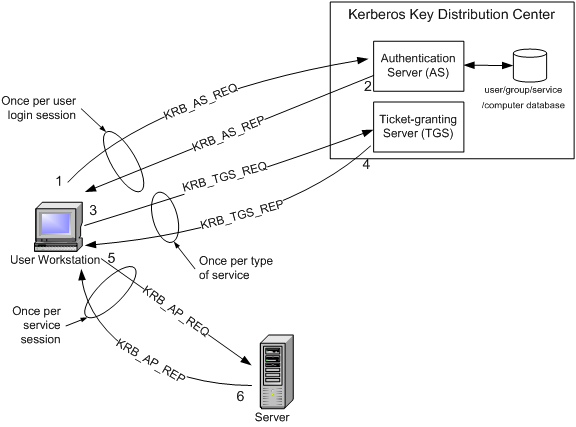
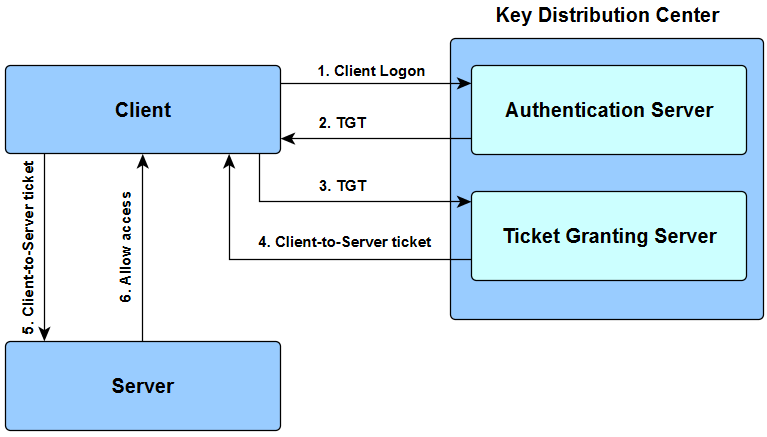
The following Kerberos V5 authentication process occurs. Basically Kerberos is a network authentication protocol that works by using secret key cryptography.
Configuring Kerberos Authentication Protocol Datasunrise Data Db Security
It has also become a standard for websites and Single-Sign-On implementations across platforms.

Kerberos authentication process. I want to explain more about steps 2 and 4. Optional Select the Enable AR authentication for bypass check box. Kerberos is an authentication protocol that is used to verify the identity of a user or host.
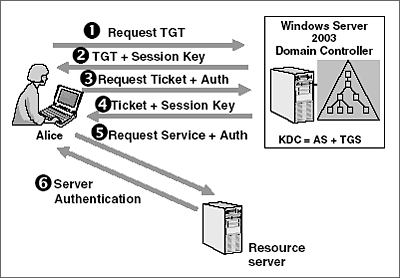
A Ticket-Granting Ticket TGT request is sent to a Kerberos KDC. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet. The Kerberos KDC returns a TGT and a session key to the PC Client.
Plain text passwords are never sent across an insecure network. Kerberos Authentication Overview. This request consists of the PC Client TGT and an authenticator.
Initial user authentication is integrated with the Winlogon single sign-on architecture. The main reasons for adopting Kerberos are. Generates a new key for the session called the session key.
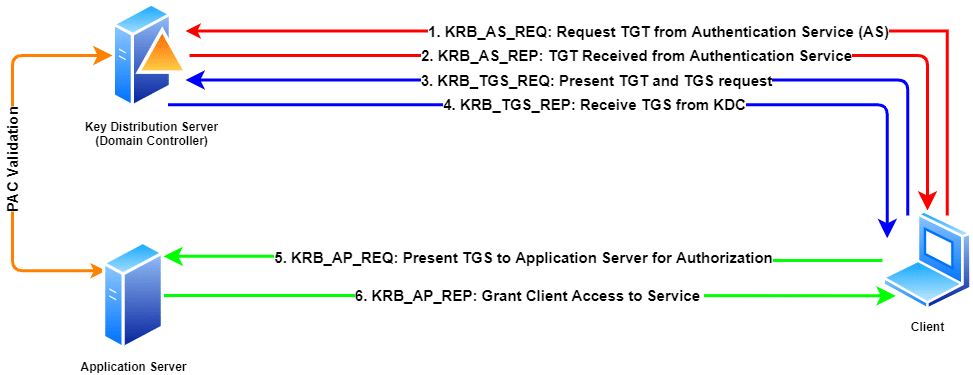
In the MIT Kerberos Ticket Manager click Get Ticket. The Kerberos V5 protocol provides a mechanism for mutual authentication between a client and a server before application data is transmitted between them. Windows Authentication Applies To.
To resolve this problem update the registry on each computer that participates in the Kerberos authentication process including the client computers. In step 2 the KDC does the following. Apple OS UNIX and Linux also use it.
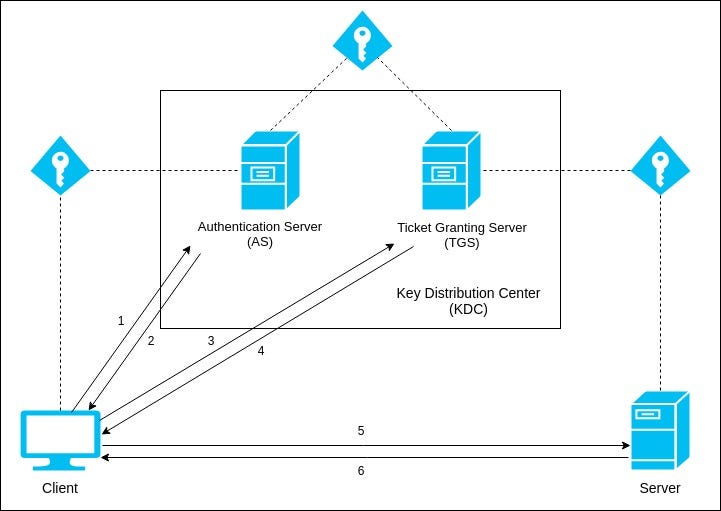
Kerberos V5 is composed of three exchanges described in detail in RFC4120 sections 11 and 3. Clients authenticate with a Key Distribution Center and get temporary keys to access locations on the network. In the Authentication Type field click KERBEROS.
This means most of us have encountered it in one place or another even if we werent aware of it. Kerberos authentication has become the default authorization tool used by Microsoft Windows. Windows Server Semi-Annual Channel Windows Server 2016.
To configure the Kerberos authentication In the left navigation panel of the Add Realm or Edit Realm page click Authentication. Overview of the Kerberos authentication process. If the authentication succeeds then your ticket information appears in the MIT Kerberos Ticket Manager.
A ticket request for the application server is sent to the Kerberos KDC. Microsoft introduced their version of Kerberos in Windows2000. Windows 7 Windows Server 2008 Windows Server 2008 R2 This topic lists Windows authentication documentation resources for the Kerberos NTLM Transport Layer SecuritySecure Sockets Layer TLSSSL Public Key Cryptography Based User-to-User PKU2U and Digest protocols in addition to links to the security.
The two servers combined make up a KDC. How Does Kerberos Authentication Work. But how does Kerberos authentication work.
This topic contains information about Kerberos authentication in Windows Server 2012 and Windows 8. Active Directory performs the functions of the KDC. Kerberos is an authentication protocol for clientserver applications.
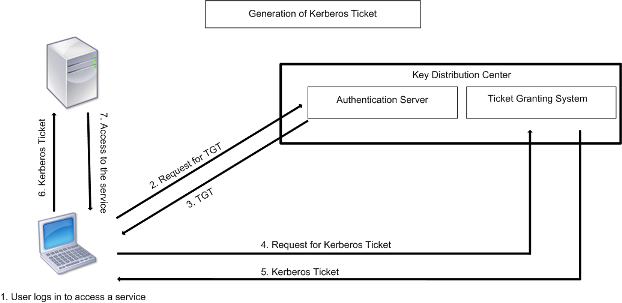
In this first post the Kerberos authentication process has been studied and the attacks has been also introduced. The following posts will show how to perform these attacks in a practical way and also how delegation works. Briefly when a client needs to request a service it does five steps as shown in the following diagram.
Kerberos also requires an Authentication Server AS to verify clients. Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux. The Kerberos authentication client is implemented as a security support provider SSP and can be accessed through the Security Support Provider Interface SSPI.
PC Client logs on the domain. Weve already established that Kerberos securely connects users and servers. I really hope that this post it helps to understand some of the more abstract concepts of Kerberos.
In the Get Ticket dialog type your principal name and password and then click OK. This protocol relies on a combination of private key encryption and access tickets to safely verify user identities. It uses secret-key cryptography and a trusted third party for authenticating client.
This allows for strong and secure authentication without transmitting passwords. Click the Start button All Programs Accessories Command Prompt. 2 minutes to read.
As part of the logon process the authenticating domain controller issues the User a ticket-granting ticket TGT. This ticket is required for User1 to be authenticated to resources. The following figure shows the sequence of events required for a client to gain access to a service using Kerberos authentication.
These are the steps in Kerberos Authentication. We recommend that you update all of your Windows-based systems especially if your users have to log on across multiple domains or forests.
Five Steps To Using The Kerberos Protocol
Kerberos Authentication Protocol Kerberos Is A Strong Network By Nipuna Dilhara Medium

The Diagram Of Kerberos Authentication Protocol Download Scientific Diagram

Kerberos Authentication An Overview Sciencedirect Topics
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
Handling Authentication Authorization And Auditing With Kerberos Ntlm
What Is Kerberos Understanding Kerberos What Is It How Does It Work

Kerberos Authentication Protocol Download Scientific Diagram

Kerberos Protocol S Topology Kerberos Authentication Includes Six Download Scientific Diagram

Kerberos Authentication Flow For Browser Based Applications Provided By The As Abap Sap Blogs

Kerberos Authentication Protocol Blog On Information Security And Other Technical Topics
Ken Schaefer Iis And Kerberos Part 1 What Is Kerberos And How Does It Work
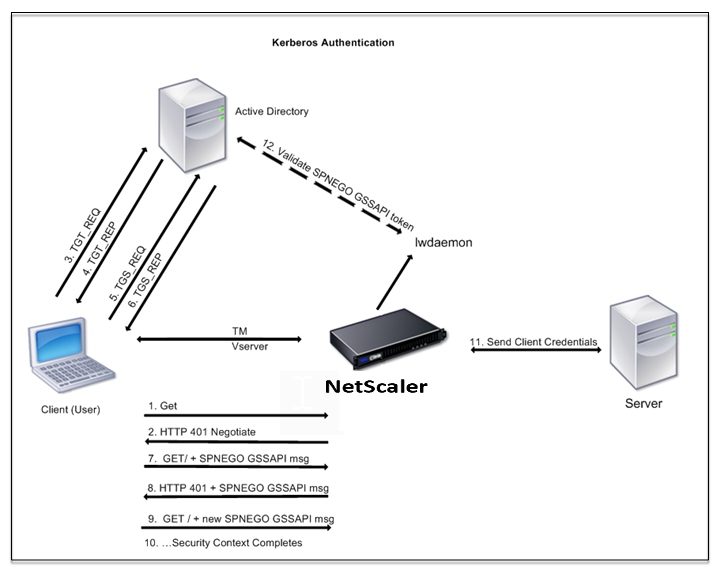
How Citrix Adc Implements Kerberos For Client Authentication

1 A Simplified Version Of The Kerberos Authentication System Both The Download Scientific Diagram